As the trend continues to move away from exploiting system services and more commonly toward exploiting client applications like web browsers and third party plugins, our research has turned towards these threats and overturned some fairly new stones for the commoditized exploit packages currently in the wild. The Storm threat, and numerous others have been using these packages to deliver driveby browser and, in this case, third party plugin exploits. These sorts of threats have been very effective recently at compromising users’ systems in order to build botnets and send spam, and steal passwords and other sensitive information.
Now, not only are these packages delivering repacked and crypted binaries via harmless looking but malicious web pages, but they are re-obfuscating the malicious content hidden on the web pages at very small intervals. The threats, at every level, are constantly changing.
We collected up these changing pages from multiple malicious web sites, de-obfuscated their code, and isolated each exploit with its shellcode to analyze them, and to identify any problems they might cause for security products. Here are some notes from our research on in-the-wild web exploits:
The code across malicious groups is becoming more and more similar. There most definitely is code sharing between the groups writing the exploits. Some of them are the exact same techniques for identical exploits.
One recent addition to the commoditized exploit packages that are bought and sold online that has not been much discussed is exploitation of a recently disclosed Yahoo Messenger vulnerability, with shellcode that evades some of the major av vendors’ security software.
The vulnerability effects a version of a component called the “Webcam Viewer Networking and Imaging” ActiveX component (ywcvwr.dll v2.0.1.4). Basically, an old-fashioned stack-based buffer overflow occurs because a 1023 byte buffer is set aside to store input for webcam functionality, but the input is not properly checked, allowing for maliciously crafted webcam objects to run arbitrary code of the attacker’s choosing.
We examined the attacker’s approach. They use a reliable method of delivering control to their shellcode on XP Sp2 and Vista systems over IE6 and IE7 with default settings: they spray the heap with shellcode of their choosing simply by creating a dozen or so variables in their javascript, and stuffing them with lots of NOP followed by shellcode. They then deliver a large amount of data (5000 bytes) to this unchecked 1023 byte buffer and overrun values on the stack, including the exception handler. An exception occurs, and because the exception handler is overwritten with an address on the heap, control is passed to their download and execute shellcode.
By default, this exploit works on Vista systems when IE6 and IE7 do not have the “Data Execution Prevention” feature enabled. But techniques to disable the DEP check even when it is enabled have been published as well.
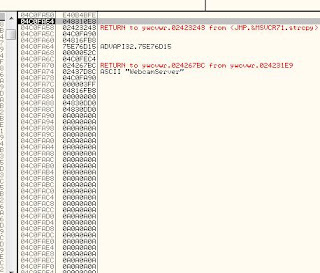
This image shows the thread stack as it is overflowed. An exception has been caused at this point, and we break on it to notice that the stack is covered with “\x0a\x0a\x0a\x0a”.
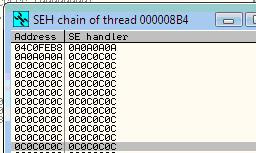
When this exception occurs, we can take a peek at the exception handler, which also is stored on the stack. It has been overwritten with “\x0a\x0a\x0a\x0a” as well. Because the exception has been thrown, our goat system tries to provide control to the first handler in the list, which happens to be at the craftily overwritten “0a0a0a0a”.
Interestingly, the heap has been sprayed with shellcode because the javascript sets up multiple variables full of shellcode. Due to this spray, the location “0a0a0a0a” now points to “0c0c0c0c”, which also is located on the heap. This heap contains two things – a nop sled of “0c0c0c0c” and “download and execute” shellcode.
Control will slide down the sled to our shellcode, and the attackers will effectively download and execute a set of binaries stored on another web server. These binaries download and execute even more malware, including bots, rootkits, password stealers, adware and other problematic software.
And whoa, they keep coming as this post is written! Another Yahoo webcam viewer vulnerability has been discovered and its exploit posted by a Chinese security group without having notified Yahoo, so we’ll keep an eye on this 0day as well and probably post on attacking activity abusing this new vulnerability. We’ve looked through the code, and it attacks a heap overflow instead of a stack overflow like this one, but methods to effectively defend against it remain the same.
Beware web sites and links that you have not visited before, especially if they are sent to you via email, and update your security software. Buffer overflow exploits like this one can turn an unwitting user into a victim.